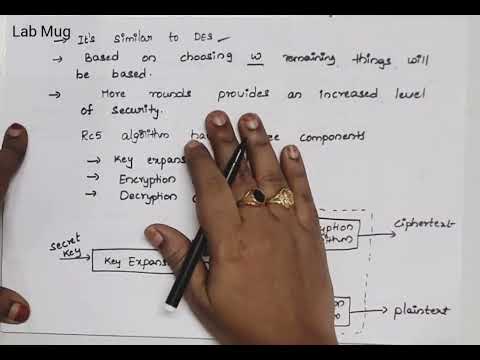
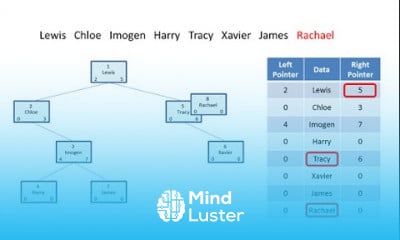
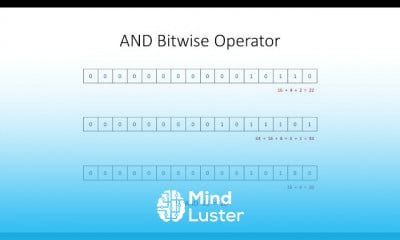
RC5 Algorithm in Cryptography and Network Security
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 25
Lesson
Comments
Related Courses in Computer Science
Course Description
Cryptography attacks course,
in this course we will learn about the various cryptography attacks used in network security. Cryptography attacks involve methods to undermine cryptographic systems, aiming to access or manipulate protected data. We will explore brute force attacks, where all possible keys or passwords are tried, and dictionary attacks, which use a list of potential passwords. Additionally, the course covers side-channel attacks that analyze secondary data like power consumption, and man-in-the-middle attacks, where the attacker intercepts and alters communication between parties. We will delve into chosen ciphertext and chosen plaintext attacks, where attackers select specific texts to uncover encryption weaknesses. Furthermore, we will examine differential cryptanalysis and linear cryptanalysis, which focus on finding patterns and relationships in ciphertexts. Timing attacks, which measure the time taken for encryption processes to infer keys, will also be discussed. By understanding these attacks, students will learn how to better protect cryptographic systems and develop more secure network security protocols. This course is essential for anyone interested in enhancing their knowledge of cybersecurity and defending against cryptographic vulnerabilities.
Trends
Creating Professional emails in excel with AI
Python programming language
Learning English Speaking
Programming basics for beginners
RPA Robotic Process Automation
Python Programming | Edureka
IT career
MS Excel
AI fundamentals for beginners
C Programming from scratch
Video editing with adobe premiere
Building a Website with HTML CSS
Cybersecurity
python programming essentials for beginners
English greetings and responses
C Programming Language
Creating bitmap images from scratch
Java Programming Language
AutoCAD 3D to 2D conversion techniques
Aprender a Programar desde
Recent
Online digital marketing from home
Creating beautiful Presentation slides
creating a marketing plan tools
growth marketing interview for beginners
digital marketing for beginners
Growth marketing career paths
Growth marketing analytics fundamentals
Growth marketing interview questions
Networking basics for beginners
Programming basics for beginners
AI fundamentals for beginners
Computer science fundamentals for beginners
Cryptocurrency basics for beginners
Computer architecture fundamentals
Cryptography basics for beginners
AutoCAD 3D to 2D conversion techniques
3D Modelling with autoCAD
AutoCAD 2D drawing essentials for beginners
Making 3D Fan blade in autoCAD
Making a Coke bottle in autoCAD 3D