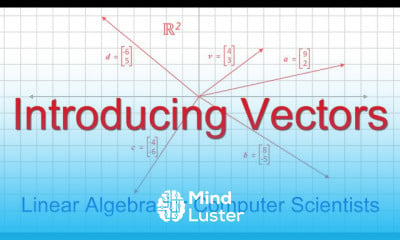
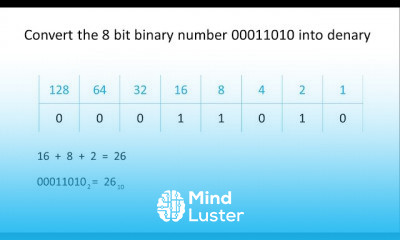
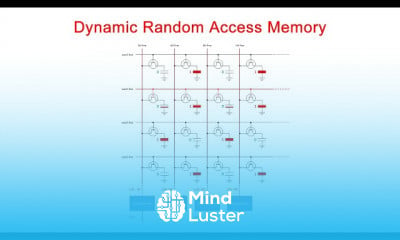
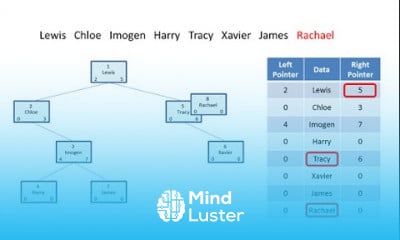
Top 7 FREE OSINT Tools How to Gather Info on Someone using OSINT
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 26
Lesson
Comments
Related Courses in Computer Science
Course Description
Nessus vulnerability scanning,
in this course you’ll learn how to use Nessus, one of the most popular vulnerability scanners, to identify and assess security weaknesses in your network. We will start with the basics of setting up and configuring Nessus, exploring its powerful features such as vulnerability detection, policy compliance, and scanning configurations. You’ll gain hands-on experience with performing scans, analyzing reports, and understanding how to interpret vulnerabilities. The course covers scanning best practices, creating custom scan policies, and automating scans for efficiency. You’ll also learn about Nessus plugins, how to update them, and manage scan results effectively. By the end of the course, you will have a solid understanding of vulnerability scanning with Nessus and be able to apply these skills to secure networks and systems, ensuring a safer IT environment. Perfect for security professionals and beginners in cybersecurity.
Trends
Cybersecurity fundamentals A Z
Web design basics
Accounting Finance course
Web Design for Beginners
E Commerce web design
Graphic design tools for beginners
Essential skills for web designers
Customizing type for logos
UX UI design career
UX design fundamentals
Create Animals icon in figma
Create food and drink icon in figma
Figma web design
Create a YouTube account on Your phone
Figma mobile app design
SQL for accountants and finance managers
Best zoology books
Web Design 101 Free Full Course
Figma mobile UI design essentials
Abstract Poster design in figma
Recent
French beans farming
Feeding stages for broilers
Dairy Production and dairy Cow farming
Bioinformatics basics
Bioinformatics databases
Vitamin A to Z tablets
Best zoology books
Best cream for piles pain
Laser surgery for piles
Best cream for piles
Anal fissure treatment
Best antibiotics for diseases
Antibodies structure
Macrophage structure
Drosophila genetics
Diagnostic tests
Bioinformatics
Genetics
Gene therapy
Kidney structure