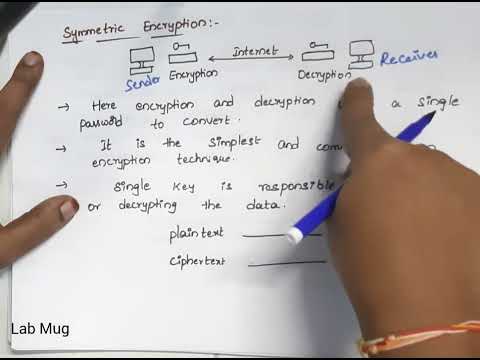
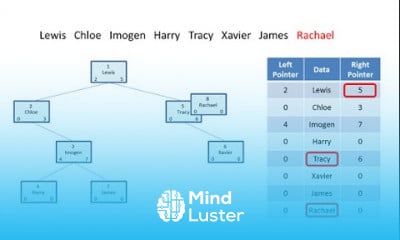
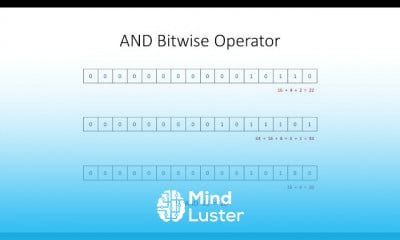
Encryption Symmetric and Asymmetric Encryption Difference between Symmetric and Asymmetric
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 25
Lesson
Comments
Related Courses in Computer Science
Course Description
Cryptography attacks course,
in this course we will learn about the various cryptography attacks used in network security. Cryptography attacks involve methods to undermine cryptographic systems, aiming to access or manipulate protected data. We will explore brute force attacks, where all possible keys or passwords are tried, and dictionary attacks, which use a list of potential passwords. Additionally, the course covers side-channel attacks that analyze secondary data like power consumption, and man-in-the-middle attacks, where the attacker intercepts and alters communication between parties. We will delve into chosen ciphertext and chosen plaintext attacks, where attackers select specific texts to uncover encryption weaknesses. Furthermore, we will examine differential cryptanalysis and linear cryptanalysis, which focus on finding patterns and relationships in ciphertexts. Timing attacks, which measure the time taken for encryption processes to infer keys, will also be discussed. By understanding these attacks, students will learn how to better protect cryptographic systems and develop more secure network security protocols. This course is essential for anyone interested in enhancing their knowledge of cybersecurity and defending against cryptographic vulnerabilities.
Trends
MS Excel
Learning English Speaking
Python programming language
Video editing with adobe premiere
English greetings and responses
ChatGPT high level
Mobile Apps from Scratch
Communication Skills
Ethical Hacking
Data Structure in C for Beginners
Magento Formation Français
English Language
python programming essentials for beginners
Business Law fundamentals
C Programming Errors and Testing
Artificial intelligence questions basics
Data structure types for beginners
Big Data Analytics skills for beginners
Influencer marketing strategies for beginners
Improve english grammar skills
Recent
Google Cybersecurity Professional Certificate
Cisco IT certifications for beginners
IBM data analyst Professional certificate
Top Programming Languages to Learn in 2024
Building a Website with HTML CSS
C Programming from scratch
Creating Unhackable Passwords with C
Most dangerous hacking gadgets in 2024
Nessus vulnerability scanning for beginners
Designing VB NET booking system form layout
Building a shark attack game in scratch
Programming with VBA for beginners
Graph data Structure
Latches and Flip Flops in digital systems
Merge Sort Algorithm techniques
Karnaugh maps with 4 variables
Array Variables in Programming
Creating a hangman game using VBA
Quicksort 2 Alternative Algorithm
Sorting algorithms for beginners