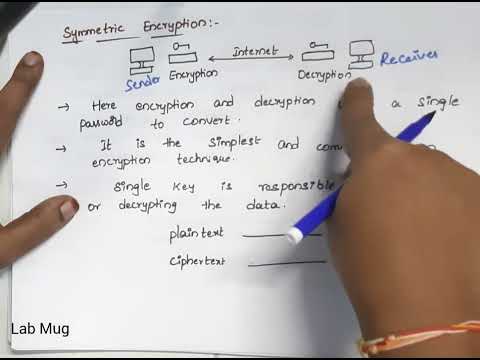
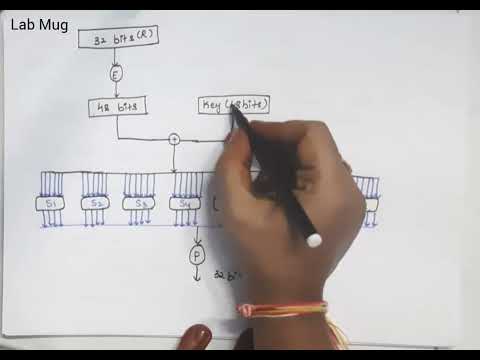
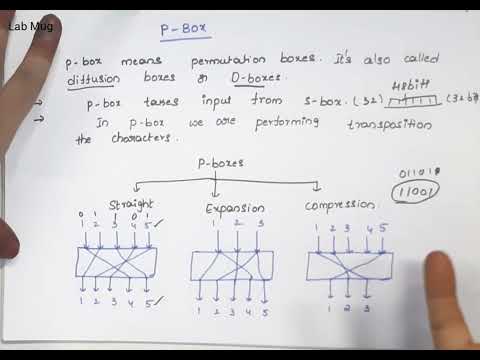
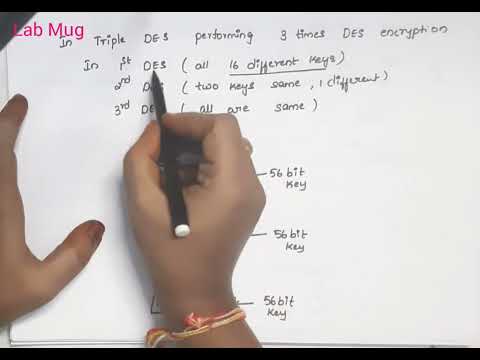
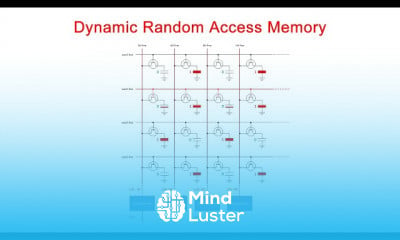
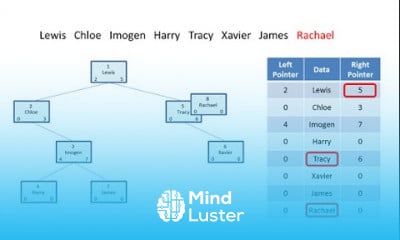
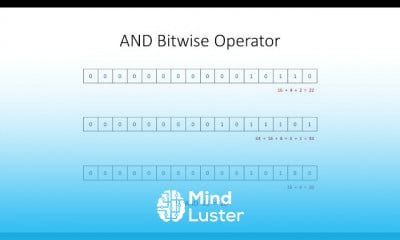
Transposition Techniques Rail Fence technique in cryptography and network security
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 25
Lesson
Comments
Related Courses in Computer Science
Course Description
Cryptography attacks course,
in this course we will learn about the various cryptography attacks used in network security. Cryptography attacks involve methods to undermine cryptographic systems, aiming to access or manipulate protected data. We will explore brute force attacks, where all possible keys or passwords are tried, and dictionary attacks, which use a list of potential passwords. Additionally, the course covers side-channel attacks that analyze secondary data like power consumption, and man-in-the-middle attacks, where the attacker intercepts and alters communication between parties. We will delve into chosen ciphertext and chosen plaintext attacks, where attackers select specific texts to uncover encryption weaknesses. Furthermore, we will examine differential cryptanalysis and linear cryptanalysis, which focus on finding patterns and relationships in ciphertexts. Timing attacks, which measure the time taken for encryption processes to infer keys, will also be discussed. By understanding these attacks, students will learn how to better protect cryptographic systems and develop more secure network security protocols. This course is essential for anyone interested in enhancing their knowledge of cybersecurity and defending against cryptographic vulnerabilities.
Trends
Learning English Speaking
Python programming language
Management from A to Z
Organization of Microcontroller
MS Excel
Digital Marketing From Scratch
Adobe illustrator tools for designers
Ethical Hacking
Mechanics of Solids basics
Complete WIFI Hacking Course Beginner to Advanced
Digital Marketing
English Language
Mobile Apps from Scratch
Medical X Ray machine basics
Human Resource Management
Photo Editing
SEO for business growth for beginners
Adobe Photoshop
Coding with programmable robots for beginners
Influencer marketing essentials
Recent
Website security basics
SEO for business growth for beginners
WordPress migration on bluehost for beginner
Influencer marketing essentials
Increase eCommerce sales ways
Content marketing works in 2024
Local SEO for multi location businesses
Ranking with google AI tools
SearchGPT for SEO and content writing
AI marketing fundamentals
Content marketing with AI tools
Inbound marketing growth strategies
Google Keyword Planner Forecasting
Google ads keyword planner forecasting
YouTube SEO techniques
Inbound marketing fundamentals
SEO for Inbound lead generation fundamentals
Surfside inbound marketing fundamentals
Google Ads conversion tracking techniques
Surfside Inbound marketing essentials