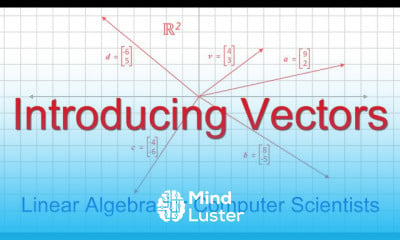
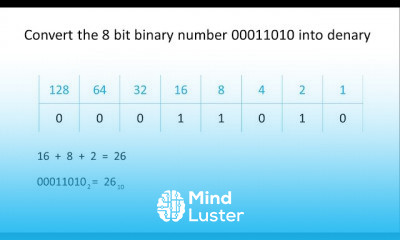
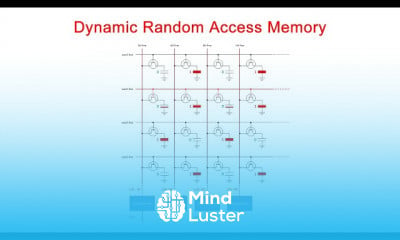
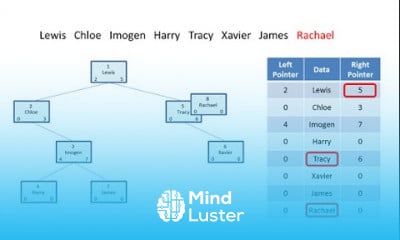
CISA Certification Domain Weighted Overview
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 31
Lesson
Comments
Related Courses in Computer Science
Course Description
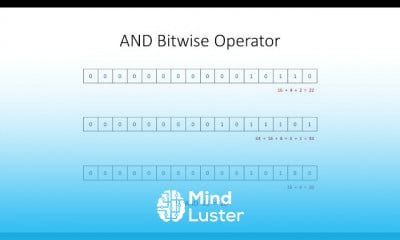
CISA - The Process of Auditing Information Systems Course: we will learn about CISA The Process of Auditing, covering essential auditing principles, risk assessment, control evaluation, and compliance. Designed for aspiring Certified Information Systems Auditors (CISA), this course provides an in-depth understanding of IT governance, audit planning, and execution. You will explore key methodologies for identifying risks, implementing controls, and ensuring compliance with industry standards. The course also focuses on best practices for auditing IT systems, analyzing vulnerabilities, and improving security frameworks. Whether you are preparing for the CISA certification or looking to enhance your auditing skills, this course will equip you with the knowledge to assess IT environments effectively and ensure organizational security and efficiency.
Trends
Graphic design tools for beginners
Excel fundamentals for finance
French
Python algorithms
Artificial intelligence essentials
Data types in python and ruby
Data Science and Data Preparation
Logo Design
Web Design for Beginners
Formation efficace à l écoute de l
C Programming
Figma for UX UI design
MS Excel
Electrical engineering for engineer
Accounting Finance course
Accounting
ESG fundamentals
Graphic Design | Photoshop
Android Photo editing app development
Learning English Speaking
Recent
ESG fundamentals
Reading financial statements
Excel fundamentals for finance
Corporate finance fundamentals
Creating a SIPOC diagram
Impact effort matrix
Staying calm at work
Prioritizing Stakeholders
One on One meetings
Business process management
Transferable skills
Communication skills for introverts
Ways to reduce stress at work for beginners
Stakeholder management
First time managers succes skills
Data types in python and ruby
Game programming project
Python algorithms
C Programming
JavaScript game programming