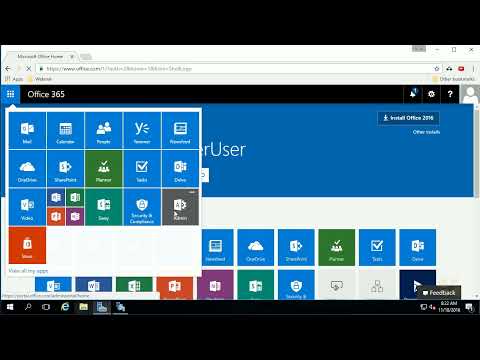
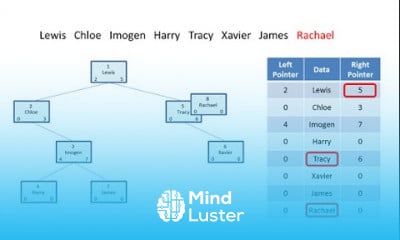
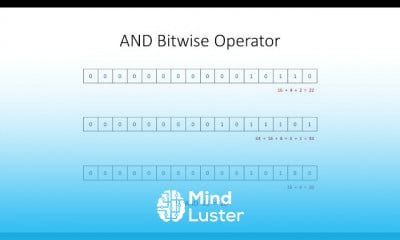
17 Web Application Proxy WAP Setup Microsoft Office 365 full course tutorial
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 19
Lesson
Comments
Related Courses in Computer Science
Course Description
MICROSOFT OFFICE 365 (IDENTITIES & REQUIREMENTS) Course: In this course, delve into the identities and requirements of Microsoft Office 365. Explore the user and administrator identities, authentication methods, and security features of Office 365. Gain insights into the technical requirements, compatibility, and integration considerations for implementing Office 365 in different environments. With comprehensive coverage and practical examples, this course equips you with the knowledge to effectively plan, deploy, and manage Office 365 identities and requirements. Whether you're an IT professional or a system administrator, this course provides valuable insights to optimize your Office 365 implementation. TUTORIAL
Trends
Learning English Speaking
MS Excel
English greetings and responses
Excel Course Basic to Advanced
Python programming language
Python for data science and AI
Creating bitmap images from scratch
AI fundamentals for beginners
Excel skills for busines intermediate
Photo Editing
Java Programming Inteview Questions for Beginners
Web development with Java spring
Online digital marketing from home
AI with IBM Watson
Video editing with adobe premiere
ISTQB advanced test analyst 2024
Digital Marketing Beginners
Creating a business marketing brand
Digital media and marketing strategies
Power BI
Recent
ISTQB advanced test analyst 2024
ISTQB exam registration guide
ISTQB test automation engineer certification
ISTQB agile technical tester 2024
ISTQB technical test analyst 2024
ISTQB mobile application tester 2024
ISTQB performance testing fundamentals
ISTQB test manager certification
ISTQB automotive software tester 2024
ISTQB certification in software testing
ISTQB foundation certification questions
Software testing bootcamp for beginners
ISTQB AI tester
ISTQB test automation engineer v2 0 exam
ISTQB foundation level exam practice
ISTQB Foundation level exam
ISTQB Agile tester practice questions
Health benefits of swimming
Swimming basics for beginners
breathe while swimming for swimmers