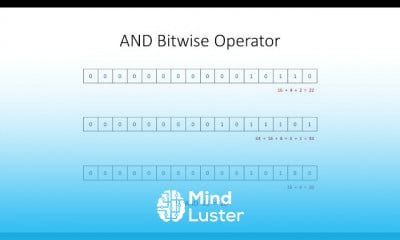
Chapter 7 Types of Mobile Security Threats
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 14
Lesson
Comments
Related Courses in Computer Science
Course Description
Secure Mobile Devices and Technology course focuses on ensuring the security of mobile devices. Explore techniques for securing smartphones, tablets, and wearable devices. Learn about secure app development, mobile device management, data encryption, and secure communication protocols. Develop skills to protect against mobile threats, such as malware and data breaches. Join this course to enhance your understanding of securing mobile devices and technology in today's digital landscape. Louay Karadsheh, PhD, CISSP, CEH, CASP
Trends
Graphic design tools for beginners
Excel fundamentals for finance
Data types in python and ruby
Data Science and Data Preparation
Web Design for Beginners
Electrical engineering for engineer
Learning English Speaking
Artificial intelligence essentials
Figma for UX UI design
YouTube channel setup
Computer Jobs
MS Excel
Formation efficace à l écoute de l
French
Advanced SQL for data analytics
ESG fundamentals
Python algorithms
Embedded Systems ES
Python programming language
Build a profitable trading
Recent
ESG fundamentals
Reading financial statements
Excel fundamentals for finance
Corporate finance fundamentals
Creating a SIPOC diagram
Impact effort matrix
Staying calm at work
Prioritizing Stakeholders
One on One meetings
Business process management
Transferable skills
Communication skills for introverts
Ways to reduce stress at work for beginners
Stakeholder management
First time managers succes skills
Data types in python and ruby
Game programming project
Python algorithms
C Programming
JavaScript game programming