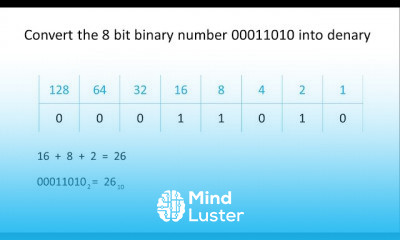
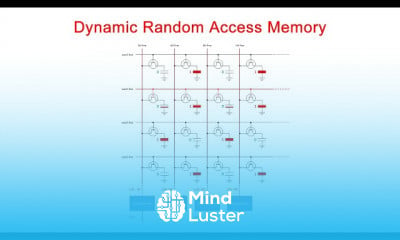
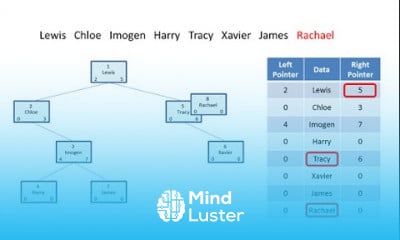
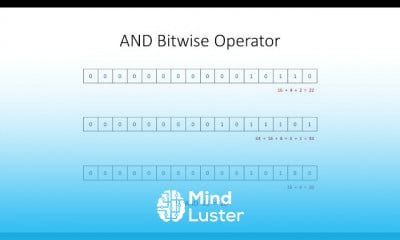
Part 2 Behavior Based Detection of Advanced Threat Detection
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 8
Lesson
Comments
Related Courses in Computer Science
Course Description
Digital Forensics course provides comprehensive training in investigating and analyzing digital evidence to uncover cybercrimes. Explore techniques for data acquisition, preservation, and analysis. Learn about computer systems, networks, and mobile devices forensics. Develop skills to identify and track digital footprints, recover deleted data, and present findings in legal proceedings. Gain hands-on experience with forensic tools and methodologies. Join this course to become a proficient digital forensics investigator and contribute to combating cybercrime. Louay Karadsheh, PhD, CISSP, CEH, CASP
Trends
Speak english fluently with confidence
MS Excel
Learning English Speaking
Building a chatbot with Python
Python programming fundamentals A Z
Generative AI tools for 2024
Creating YouTube videos for beginners
Excel Course Basic to Advanced
Python programming language
Content marketing for beginners
Center of Mass in Physics
Marketing basics for beginners
Phrasal Verbs in daily conversations
Web Development Tools Essentials
Data Science with Python for beginners
AI tools for business for beginners
Coding tools for developers
Google analytics 4 for beginners
Tools and toolbar in Photoshop for beginners
WordPress Complete Course in Hindi
Recent
Arabic numbers for beginners
Rating arabic handwriting techniques
Form verbal sentences in arabic
Arabic sentence structure for beginners
Phrasal Verbs in daily conversations
Speak english fluently with confidence
Rules for plural forms of irregular nouns
English slang dictionary for fluency
English idioms for everyday conversations
Native english vocabulary for fluency
Teach reading with Phonics for beginners
English speaking confidence techniques
Business english communication skills
American english conversation for beginners
Advanced english listening and vocabulary
English prepositions for beginners
Improve english Pronunciation for beginners
PGP in data science and engineering
Building a chatbot with Python
Python programming fundamentals A Z