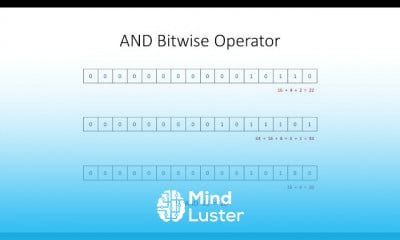
15 Processes In An Information Security Strategy ISACA CISM DOMAIN 1 INFORMATION SECURITY GOVERNANCE
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 339
Lesson
Show More
Lessons
Comments
Related Courses in Computer Science
Course Description
CISM ISACA COMPLETE course provides comprehensive training on the Certified Information Security Manager (CISM) certification. Explore key domains of information security management, risk assessment, incident response, and governance. Gain expertise in developing and managing information security programs aligned with organizational goals. Learn best practices, industry standards, and strategies to protect critical information assets. Join this course to master CISM concepts, enhance your career prospects, and contribute to effective information security governance in organizations. TUTORIAL
Trends
Learning English Speaking
CANVA templates for beginners
Folder sharing in google drive for beginners
Pencil Drawing Tutorials
Python for data science and AI
Video editing with adobe premiere
Managerial accounting fundamentals
Cryptocurrency Blockchain for beginners
MS Excel
Real Estate Investors
Emotional Intelligence
Thermodynamics fundamentals for engineers
Python Object Oriented Programming
Organic Chemistry Exam Strategies
Soldering Iron repair for beginners
Android programmation mobile
Excel assessment test for job interview
Creating bitmap images from scratch
Improve your day to day English
Sagging breast exercises at home
Recent
Building arduino robots and devices
Thermodynamics fundamentals for engineers
Excel skills for busines intermediate
Machine learning by stanford university
Digital manufacturing and design principles
Machine learning foundations
Web development with Java spring
AI with IBM Watson
environmental law and policy principles
Creating a business marketing brand
Financial markets coursera quiz answer
CISCO cybersecurity exam questions
Resume and CV writing basics
Excel skills for business specialization
Digital media and marketing strategies
IBM cybersecurity analyst certificate
AWS identity and access management
Financial safety in cyberspace
DXC Technology Job recruitment
UX design foundations for beginners