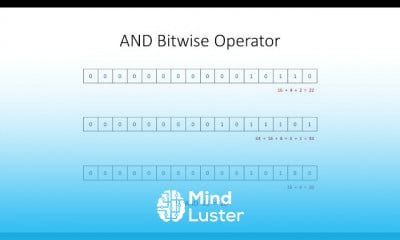
6 Information Security Management ISACA CISM COURSE DOMAIN 1 INFORMATION SECURITY GOVERNANCE
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 339
Lesson
Show More
Lessons
Comments
Related Courses in Computer Science
Course Description
CISM ISACA COMPLETE course provides comprehensive training on the Certified Information Security Manager (CISM) certification. Explore key domains of information security management, risk assessment, incident response, and governance. Gain expertise in developing and managing information security programs aligned with organizational goals. Learn best practices, industry standards, and strategies to protect critical information assets. Join this course to master CISM concepts, enhance your career prospects, and contribute to effective information security governance in organizations. TUTORIAL
Trends
AI powered Digital Marketing for Beginners
MS Excel
Learning English Speaking
ChatGPT essentials for beginners
Python programming language
Excel Course Basic to Advanced
Video editing with adobe premiere
Building a Website with HTML CSS
Cybersecurity
Creating bitmap images from scratch
C Programming from scratch
Organization of Microcontroller
English greetings and responses
Electronics fundamentals for beginners
Communication Skills
App in Android
Javascript interview questions and answers
CompTIA security certification for beginners
Data Entry for Beginners
Power BI
Recent
ChatGPT essentials for beginners
CompTIA security certification for beginners
Highest Paying IT certifications
Javascript interview questions and answers
Azure fundamentals certification exam
IT certification exams Preparation
Cyber security roadmap for beginners
AWS certification Learning Paths for beginner
Google Cybersecurity Professional Certificate
Cisco IT certifications for beginners
IBM data analyst Professional certificate
Top Programming Languages to Learn in 2024
Building a Website with HTML CSS
C Programming from scratch
Creating Unhackable Passwords with C
Most dangerous hacking gadgets in 2024
Nessus vulnerability scanning for beginners
Designing VB NET booking system form layout
Building a shark attack game in scratch
Programming with VBA for beginners