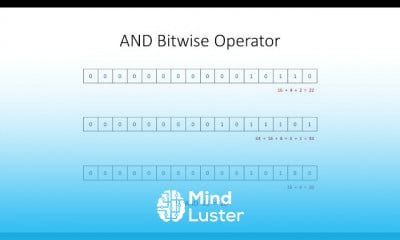
The Ticking Time Bomb Simple hacker techniques that cause major cyber incidents
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 4
Lesson
Comments
Related Courses in Computer Science
Course Description
Cybersecurity course equips participants with essential knowledge and skills to protect digital systems and data from cyber threats. Explore various cybersecurity domains, including network security, application security, endpoint security, data security, and cloud security. Learn about threat detection, incident response, vulnerability assessment, and risk management. Gain practical insights into implementing security controls, secure coding practices, and security best practices. Join this course to enhance your cybersecurity proficiency, mitigate risks, and safeguard organizations from evolving cyber threats in today's digital landscape. Inside Cloud and Security
Trends
Electrical engineering for engineer
Graphic design tools for beginners
Web Design for Beginners
Artificial intelligence essentials
Distributed Systems
YouTube channel setup
Build a profitable trading
Human Resources Management
Build a tic tac Toe app in Xcode
Earn money with chatGPT
Microsoft Word
Making money with apps
American english speaking practice
Python for beginners
Microsoft Excel
Certified in CyberSecurity
Marketing basics for beginners
Cyber Security for Beginners | Edureka
Ethical Hacking
Theory of computation fundamentals
Recent
Bioinformatics basics
Bioinformatics databases
Vitamin A to Z tablets
Best zoology books
Best cream for piles pain
Laser surgery for piles
Best cream for piles
Anal fissure treatment
Best antibiotics for diseases
Antibodies structure
Macrophage structure
Drosophila genetics
Diagnostic tests
Bioinformatics
Genetics
Gene therapy
Kidney structure
DNA replication and types
Bacterial cell structure
Parasite structure