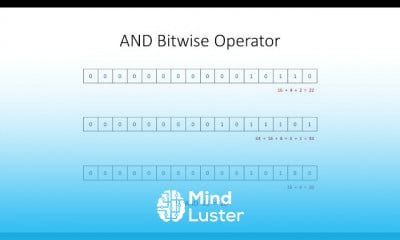
What is SOAR Security Orchestration Automation Response
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 4
Lesson
Comments
Related Courses in Computer Science
Course Description
Endpoint detection strategies course,
in this course we explore comprehensive approaches to safeguarding network endpoints against emerging cyber threats. This course delves into various strategies and methodologies aimed at identifying, mitigating, and responding to potential security breaches targeting individual devices within a network. Participants will learn about the latest trends, tools, and techniques employed in endpoint detection, including advanced threat intelligence, behavior analysis, anomaly detection, and signature-based detection methods. Through practical examples and case studies, learners will gain insights into designing and implementing effective endpoint detection strategies tailored to diverse organizational needs and risk profiles. Whether you're a cybersecurity professional seeking to enhance threat detection capabilities or an IT administrator tasked with bolstering endpoint security posture, this course equips you with the knowledge and skills needed to proactively defend against evolving cyber threats targeting network endpoints. IBM Technology
Trends
Video editing with adobe premiere
MS Excel
Learning English Speaking
Python programming language
Create a website with wordPress for beginners
Mobile Apps from Scratch
Digital Marketing
English skills with books and movies
Data Entry
Marketing
Ethical Hacking
Communication Skills
Excel Course Basic to Advanced
Photo Editing
SEO for business growth for beginners
Excel Power Query in excel for beginners
Data Science with Python conditions
Draw Faces for Beginners
Draw Faces for Beginners
The Complete Python Programming Full Course
Recent
Comparison of equity and preference shares
Source documents in accounting beginners
English greetings and responses
Improve english grammar skills
English spelling rules for beginners
English pronunciation and spelling basics
English modal verbs essentials
FCE exam preparation essentials
B1 preliminary speaking exam Preparation
CAE exam preparation essentials
Business english phrases and idioms
Weather expressions in english for beginners
Adjectives and adverbs in english
Everyday english expressions for beginners
Interactive english for Job interviews
Conversation skills for beginners
English grammar essentials for beginners
Card game vocabulary in english
Phrasal verbs in business english
English skills with books and movies