Physics Revision Trigonometery II
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 3
Lesson
Comments
Related Courses in Mathematics
Course Description
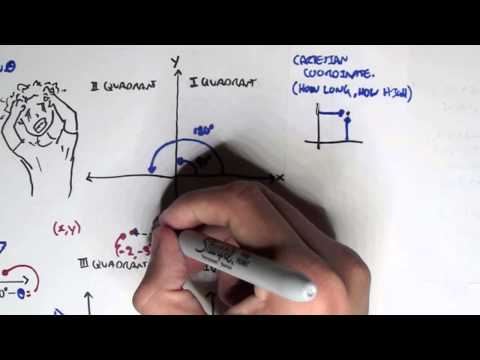
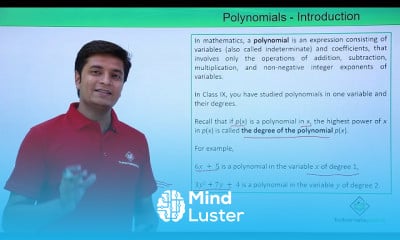
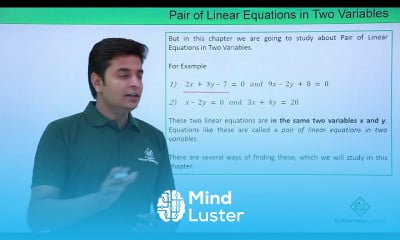
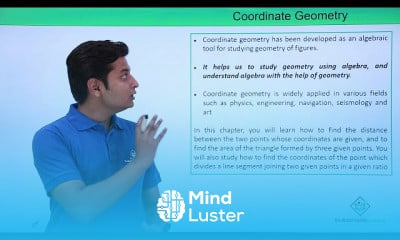
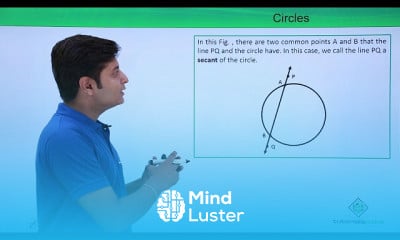
Trigonometery II course,
in this course we delve deeper into the study of trigonometric functions and their applications. Building upon the foundations established in Trigonometry I, we explore advanced topics such as trigonometric identities, inverse trigonometric functions, trigonometric equations, and their graphical representations. Additionally, we examine the use of trigonometry in solving complex problems involving triangles, vectors, and periodic phenomena. Through theoretical discussions and practical exercises, students will gain a comprehensive understanding of trigonometry's role in mathematics and its applications in various fields, including physics, engineering, and astronomy.
Trends
Graphic design tools for beginners
Microsoft Excel
Artificial intelligence essentials
Compiler Design Principles
Build a profitable trading
Network analysis Ankit goyal
Essential english phrasal verbs
YouTube channel setup
Build a tic tac Toe app in Xcode
Excel skills for math and science
American english speaking practice
Computer science careers
Learning English Speaking
Making money with apps
Ubuntu linux
MS Excel
Python for beginners
Human Resources Management
Marketing basics for beginners
Bioinformatics basics
Recent
Bioinformatics basics
Bioinformatics databases
Vitamin A to Z tablets
Best zoology books
Best cream for piles pain
Laser surgery for piles
Best cream for piles
Anal fissure treatment
Best antibiotics for diseases
Antibodies structure
Macrophage structure
Drosophila genetics
Diagnostic tests
Bioinformatics
Genetics
Gene therapy
Kidney structure
DNA replication and types
Bacterial cell structure
Parasite structure