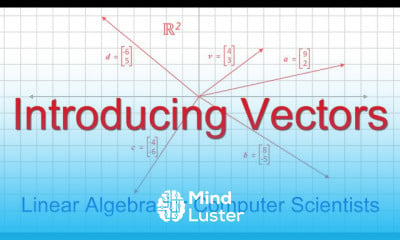
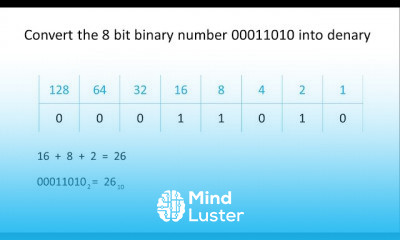
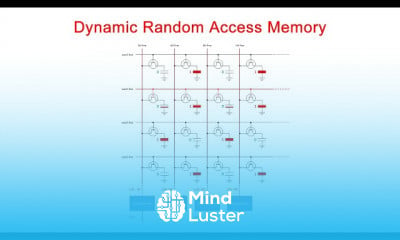
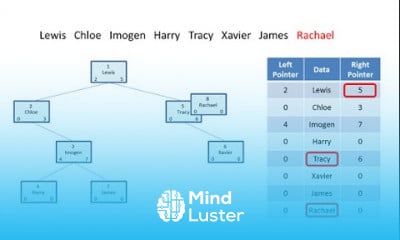
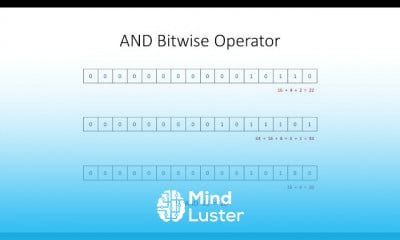
Understanding cyber threats Locs and Attack Methodology | Certified SOC Analyst CSA Tutorial
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 5
Lesson
Comments
Related Courses in Computer Science
Course Description
Security Operations course,
In this course, you'll gain expertise in Security Operations, including threat detection, incident response, and cybersecurity strategies.
Trends
AUTOMATA THEORY
MS Excel
Video editing with adobe premiere
Learning English Speaking
Control Systems CS
Create a website with wordPress for beginners
Python programming language
Mobile Apps from Scratch
Digital Marketing
English greetings and responses
C Programming Language
Electronics fundamentals for beginners
R Programming basics for Data Analytics
English Language
Data Science with Python conditions
IC engine parts in Mechanical Engineering
Advanced Soil Mechanics course
Digital Logic Families in Digital Electronics
English Grammar
Business Law fundamentals
Recent
Royalty accounts fundamentals
Format of container accounts for beginners
company accounts fundamentals
Branch accounting fundamentals
Business Law fundamentals
Coordination in management
Influencer marketing strategies for beginners
Micro and macro economics for beginners
Job analysis techniques and tools
Total quality management for beginners
Golden rules of accounting with example
Comparison of equity and preference shares
Source documents in accounting beginners
English greetings and responses
Improve english grammar skills
English spelling rules for beginners
English pronunciation and spelling basics
English modal verbs essentials
FCE exam preparation essentials
B1 preliminary speaking exam Preparation