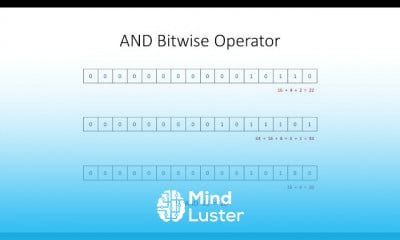
What is Scanning In Ethical Hacking | How to use Scanning in Ethical Hacking | InfosecTrain
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 21
Lesson
Comments
Related Courses in Computer Science
Course Description
Network Topology Types course,
In this course we will explore various network topology types, their configurations, advantages, and drawbacks
Trends
Web Design for Beginners
Logo Design
Graphic Design Basics
Web Design Using HTML CSS
Building a chatbot with Python
Graphic Design | Photoshop
Web Design 101 Free Full Course
Accounting
Designing text effects in photoshop for beginners
Accounting Finance course
Creative 3D logos in illustrator CC
Financial Accounting
Create a YouTube account on Your phone
Flask python for beginners
Figma Signing Up and Signing In
Generative AI tools for 2024
Figma UI design Playground basics
Test graphic design skills for beginners
company accounts fundamentals
Content marketing for beginners
Recent
PGP in data science and engineering
Building a chatbot with Python
Python programming fundamentals A Z
Data Science with Python for beginners
Python machine learning for beginners
Python OOPs concepts for beginners
PyGame Python for beginners
Generative AI tools for 2024
Careers in cybersecurity for engineer
Cybersecurity fundamentals A Z
Data visualization tools for beginners
Python project ideas
Data structures and algorithms in python
Python IDE types
Using ChatGPT for excel
Python for machine learning projects
Python for data science Projects
Build E Commerce website using HTML
Flask python for beginners
Amazon S3 for beginners